What is a VPN? What are the different types of virtual private network
A virtual private network, better known as a VPN, protects your identity and browsing activity from hackers, businesses, government agencies, and other snoops. When connecting to the internet, your data and IP address are hidden by a type of virtual tunnel. This keeps others from spying on your online activity.
A virtual private network gives you online privacy and anonymity by creating a private network from a public internet connection.
VPNs mask your internet protocol (IP) address so your online actions are virtually untraceable. Most important, VPN services establish secure and encrypted connections to provide greater privacy than even a secured Wi-Fi hotspot.
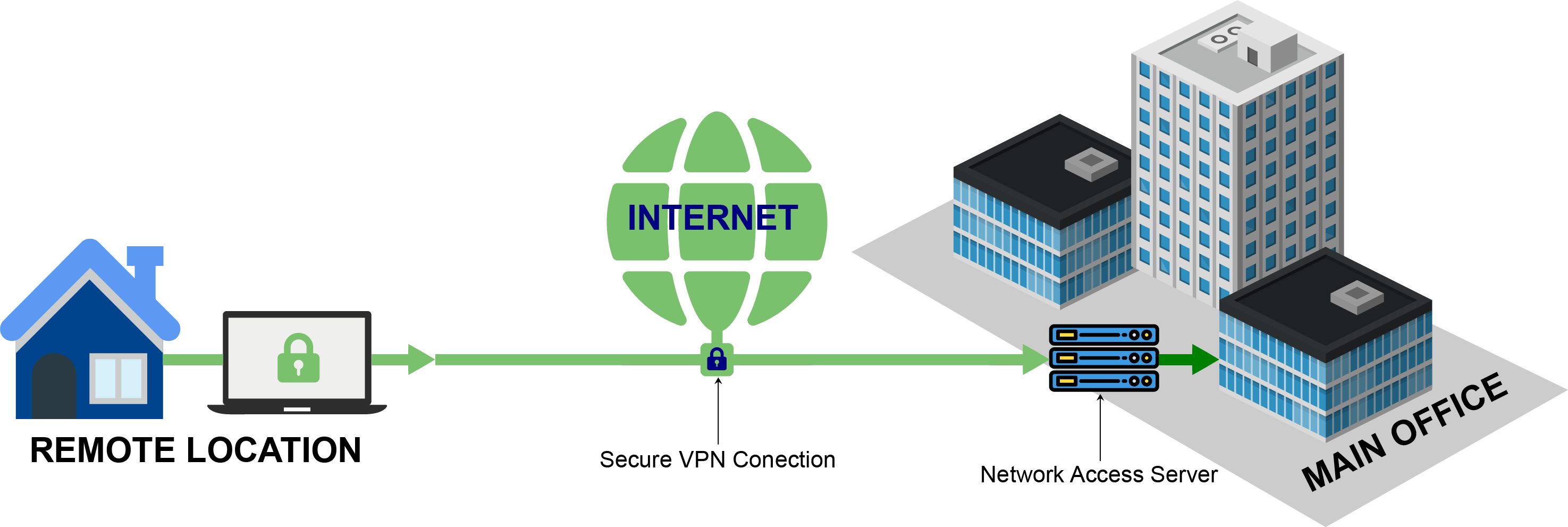
VPN technology was developed to provide access to corporate applications and resources to remote users, mobile users, and branch offices. For security, the private network connection may be established using an encrypted layered tunneling protocol, and users may be required to pass various authentication methods to gain access to the VPN.
A VPN available from the public Internet can provide some of the benefits of a wide area network (WAN). From a user perspective, the resources available within the private network can be accessed remotely.
Virtual Private Network is basically of 2 types:
Remote Access VPN: Remote Access VPN permits a user to connect to a private network and access all its services and resources remotely.
Site to Site VPN: A Site-to-Site VPN is also called as Router-to-Router VPN and is commonly used in large companies.
- Intranet-based VPN: When several offices of the same company are connected using Site-to-Site VPN type, it is called an Intranet-based VPN.
- Extranet based VPN: When companies use a Site-to-site VPN type to connect to the office of another company, it is called an Extranet based VPN.
Types of Virtual Private Network (VPN) Protocols:
- Internet Protocol Security (IPSec):
Internet Protocol Security, known as IPSec, is used to secure Internet communication across an IP network. IPSec secures Internet Protocol communication by verifying the session and encrypts each data packet during the connection.
IPSec runs in 2 modes:
- (i) Transport mode
- (ii) Tunneling mode
The work of transport mode is to encrypt the message in the data packet and the tunneling mode encrypts the whole data packet. IPSec can also be used with other security protocols to improve the security system.
Layer 2 Tunneling Protocol (L2TP):
L2TP or Layer 2 Tunneling Protocol is a tunneling protocol that is often combined with another VPN security protocol like IPSec to establish a highly secure VPN connection. L2TP generates a tunnel between two L2TP connection points and the IPSec protocol encrypts the data and maintains secure communication between the tunnel.
Point–to–Point Tunneling Protocol (PPTP):
PPTP or Point-to-Point Tunneling Protocol generates a tunnel and confines the data packet. Point-to-Point Protocol (PPP) is used to encrypt the data between the connection. PPTP is one of the most widely used VPN protocol and has been in use since the early release of Windows. PPTP also uses on Mac and Linux apart from Windows.
SSL and TLS:
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) generate a VPN connection where the web browser acts as the client and user access is prohibited to specific applications instead of the entire network. Online shopping websites commonly use SSL and TLS protocol. It is easy to switch to SSL by web browsers and with almost no action required from the user as web browsers come integrated with SSL and TLS. SSL connections have “HTTPS” in the initial of the URL instead of “HTTP”.
OpenVPN:
OpenVPN is an open-source VPN that is commonly used for creating Point-to-Point and Site-to-Site connections. It uses a traditional security protocol based on SSL and TLS protocol.
Secure Shell (SSH):
Secure Shell or SSH generates the VPN tunnel through which the data transfer occurs and also ensures that the tunnel is encrypted. The SSH connection is generated by an SSH client and data is a transfer from a local port onto the remote server through the encrypted tunnel.
What is a vpn connection and how does it work
A VPN extends a corporate network through encrypted connections made over the Internet. Because the traffic gets encrypts between the device and the network, traffic remains private as it travels. An employee can work outside the office and still securely connect to the corporate network. Even smartphones and tablets can connect through a VPN.
VPN service
A wide variety of (typically commercial) entities provide “VPNs” for all kinds of purposes, but depending on the provider and the application, they often do not create a true “private network” with anything meaningful on the local network.
On the client-side, a common virtual private network setup is by design not a conventional VPN but does typically use the operating system’s VPN interfaces to capture a user’s data to send through. This includes virtual network adapters on computer OSes and specialized “VPN” interfaces on mobile operating systems. A less common alternative is to provide a SOCKS proxy interface.
Is it safe to use a virtual private network?
A quality VPN is a safer way to search the internet. Without a virtual private network, your browsing and downloading activity could be visible to hackers, snoops, and cybercriminals. A hacker could intercept your email messages, mine personal data such as your Social Security number, or uncover the password to your online banking portal or credit card.
Any of this could expose you to identity theft or fraud. That’s why logging onto a virtual private network, which protects your privacy, is one of the safest ways to browse the web.
Join Telegram Group of Daily Jobs Updates for 2010-2023 Batch: Click Here
If You Want To Get More Daily Such Tech Updates, Career Advice Then Join the Telegram Group From Above Link And Never Miss Update.
Wipro Elite NLTH 2021 Registration: Click here
Accenture Hiring Freshers of Package 4.5 LPA Across India: Click here
Why You’re Not Getting Response From Recruiter?: Click here
Top 5 High Salary Jobs in India IT Sector 2020: Click here
How To Get a Job Easily: Professional Advice For Job Seekers: Click here
A Leadership Guide For How To Win Hearts and Minds: Click here
COVID-19 Live Tracker India & Coronavirus Live Update: Click here
Career Tips for Freshers: Top 7 Hacks To Land Your Target Job: Click here
Top 5 Best Indian Car Launches In December ahead: Click here
Feel Like Demotivated? Check Out our Motivation For You: Click here
Top 5 Best Mobile Tracking App in 2021 For Mobile & PC: Click here
5 Proven Tips For How To Look Beautiful and Attractive: Click here
Home Workouts During The Lockdown For Fitness Freaks: Click here